With the steady rise in ransomware attacks and success, it’s highly likely that related phishing variants will continue to permeate the landscape in 2018.
While this is not a new threat, it’s one that you want to be truly prepared to face. With that in mind, we looked back into our 2017 data and what we found is good news for those clients running active threat ransomware simulations in their environment.
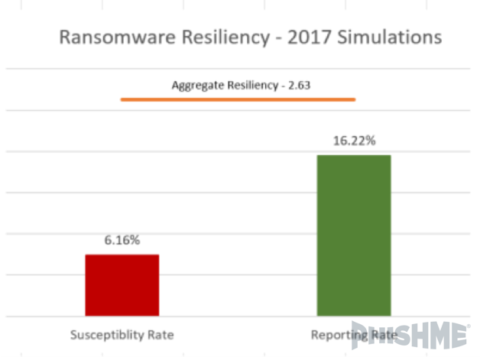
Across 246 simulations and more than 712k emails, the aggregate resiliency score was 2.63. This means that for every susceptible user, there were more than 2 that reported the threat in our simulations.
What this ultimately shows us is that clients can develop recognition and reporting capabilities for these types of attacks when active threat templates are used in immersive simulations. Further, it indicates that these organizations are better prepared to mitigate this threat should it materialize in their environments.
As we have discussed in past blogs, these results highlight the importance of understanding what your organization is seeing in terms of real attacks and that anti-phishing programs should focus on those threats to mitigate the risk of breach.
This represents a fundamental shift in how we think about getting ahead of hackers, APTs and other malicious actors. In the past, the conversation has always been about how fast we identify a breach after the fact.
Now, it’s about utilizing “crowd sourcing” as a strategy to catch hackers in the act.
At PhishMe®, we do this by ensuring our anti-phishing programs include spear-phishing simulations that target high value, at-risk users with scenarios that mimic real world attacks. Each immersive simulation includes reporting instructions for those that fall susceptible and conditions users to do their part for organizational security.
How to Pay It Forward
Utilize multiple intelligence sources to identify exactly who is being targeted by what type of phish and mimic those attacks on a broader scale to drive recognition and reporting of specific threats.
- Work with your intel and incident response teams to identify active phishing attacks against your organization.
- Model simulations based on those identified threats.
- Stress the importance of reporting for all users that recognize a phish (even in the event of susceptibility).
- Repeat low resiliency simulations to improve performance and increase organizational capabilities.
Take Action
As the data in this blog shows, we can prepare an organization’s users to resist active threats.
The key is developing the ability to act on what is being reported. In other words, until we analyze reports of suspected phishing attacks we are only collecting intelligence data.
It’s time to take that data and make it actionable.
Current PhishMe Triage™ Managed Services data shows us that 10% of reported (suspected) phish are, in fact, malicious. This means that 10 out of every 100 suspected phish that made it past your perimeter defense have the potential to cause a breach.
It’s through analysis of those reports and mitigation of validated threats that we pay ourselves (by reducing value at risk) and avoid paying ransoms to malicious actors. The companies in our data set above are prepared to do just that.
Are you?
To learn more about becoming more resilient to phishing, download the 2017 Enterprise Phishing Resiliency and Defense Report.