Phishing Security Awareness Training
Train your employees to defend against advanced email threats.
Leverage the most powerful security awareness training platform on the market.
World-class security awareness training with Cofense PhishMe.
Condition your workforce against today's latest threats and transform them into your strongest line of defense.
Real & Relevant Threat Simulations
Train your employees on real threats bypassing secure email gateways.
- Insights from Cofense Intelligence, Cofense Labs and Cofense Phishing Defense Center (PDC) feed real, current threats into our phishing simulation.
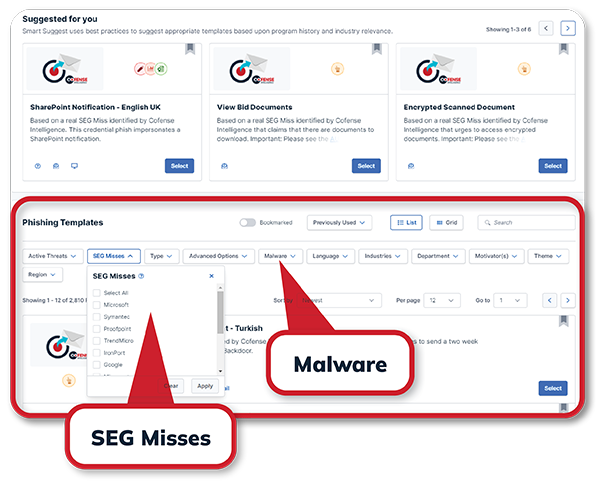
- Search for scenarios based on phish observed to bypass Secure Email Gateways (SEGs), including those deployed at your organization—simply use the SEG Misses filter.
- With our SEG miss templates, you can find email threat scenarios, like BEC, matching attacks against your company or industry.
Expansive Content Library
Empower your team with award-winning security awareness training content.
- Choose your favorites from an innovative and ever-expanding training library.
- Import your own lessons and manage your Cofense and non-PhishMe learning materials in one place.
- New content is added monthly to ensure relevancy to what’s happening in the market.
- Educate your users with engaging content in a variety of forms: animation, gaming, live-action, adaptive learning, micro-learnings and more!
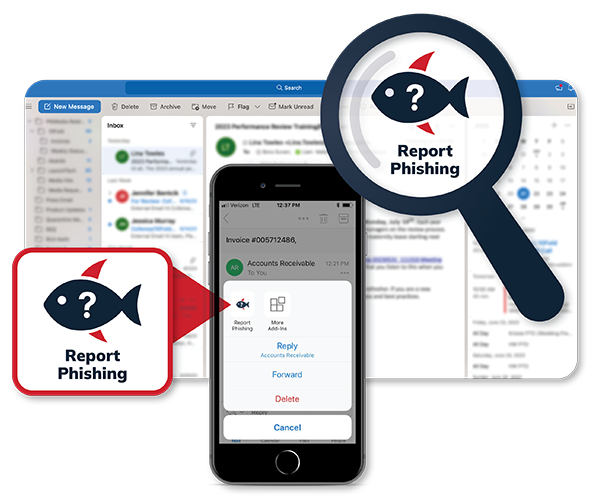
One-Click Threat Reporting
Instantly allow users to report suspected threats.
- Cofense Reporter button is right there in their email toolbar so users have a constant reminder to report anything suspicious.
- Customers who deploy our solution enjoy reporting rates at least twice as high as those that don’t.
- Only potentially real phish get reported to the SOC, not emails from phishing simulations, easing the burden on threat responders.
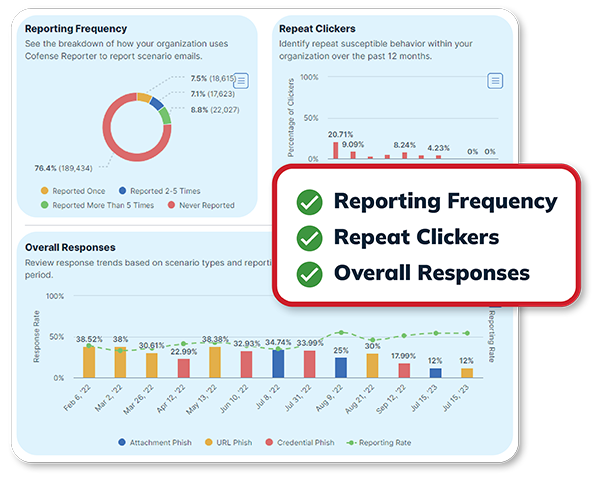
Robust Program Analytics
See the effectiveness of your SAT program with real-time insights.
- Combine reporting data to understand and predict how users are likely to react during a real phishing attack to understand program effectiveness and resilience.
- Board Reports allow your executives to monitor company performance and track the change in organizational resiliency to email attacks.
- By encouraging end users to report suspicious emails quickly, you can switch your program focus from click rates to overall reporting, the metric that truly matters.